Windows Server 2019. Download / Install (01) Download CentOS 8 (02) Install CentOS 8. By default setting of HAproxy, logs are sent to local2 facility, so. Haproxy for windows (it is very easier to transfer others server) QuickStart(use quiet mode) haproxy.exe -f config.json -q These 3 files is required for running haproxy.exe cyggccs-1.dll cygwin1.dll.
Overview
Download haproxy packages for Alpine, ALT Linux, Arch Linux, CentOS, Debian, Fedora, FreeBSD, NetBSD, OpenMandriva, openSUSE, OpenWrt, Slackware, Ubuntu.
If your application makes use of SSL certificates, then some decisions need to be made about how to use them with a load balancer.
A simple setup of one server usually sees a client's SSL connection being decrypted by the server receiving the request. Because a load balancer sits between a client and one or more servers, where the SSL connection is decrypted becomes a concern.
There are two main strategies.
Haproxy Windows Download Windows 10
SSL Termination is the practice of terminating/decrypting an SSL connection at the load balancer, and sending unencrypted connections to the backend servers.
This means the load balancer is responsible for decrypting an SSL connection - a slow and CPU intensive process relative to accepting non-SSL requests.
Haproxy Windows Download Version
This is the opposite of SSL Pass-Through, which sends SSL connections directly to the proxied servers.
With SSL-Pass-Through, the SSL connection is terminated at each proxied server, distributing the CPU load across those servers. However, you lose the ability to add or edit HTTP headers, as the connection is simply routed through the load balancer to the proxied servers.
This means your application servers will lose the ability to get the X-Forwarded-* headers, which may include the client's IP address, port and scheme used.
Which strategy you choose is up to you and your application needs. SSL Termination is the most typical I've seen, but pass-thru is likely more secure.
There is a combination of the two strategies, where SSL connections are terminated at the load balancer, adjusted as needed, and then proxied off to the backend servers as a new SSL connection. This may provide the best of both security and ability to send the client's information. The trade off is more CPU power being used all-around, and a little more complexity in configuration.
An older article of mine on the consequences and gotchas of using load balancers explains these issues (and more) as well.
HAProxy with SSL Termination
Pokemon mega emerald xy rom. We'll cover the most typical use case first - SSL Termination. As stated, we need to have the load balancer handle the SSL connection. This means having the SSL Certificate live on the load balancer server.
We saw how to create a self-signed certificate in a previous edition of SFH. We'll re-use that information for setting up a self-signed SSL certificate for HAProxy to use.
Keep in mind that for a production SSL Certificate (not a self-signed one), you won't need to generate or sign a certificate yourself - you'll just need to create a Certificate Signing Request (csr) and pass that to whomever you purchase a certificate from.
First, we'll create a self-signed certificate for *.xip.io, which is handy for demonstration purposes, and lets use one the same certificate when our server IP addresses might change while testing locally. For example, if our local server exists at 192.168.33.10, but then our Virtual Machine IP changes to 192.168.33.11, then we don't need to re-create the self-signed certificate.
I use the xip.io service as it allows us to use a hostname rather than directly accessing the servers via an IP address, all without having to edit my computers' Host file.
As this process is outlined in a passed edition on SSL certificates, I'll simple show the steps to generate a self-signed certificate here:
This leaves us with a xip.io.csr, xip.io.key and xip.io.crt file.
Next, after the certificates are created, we need to create a pem file. A pem file is essentially just the certificate, the key and optionally certificate authorities concatenated into one file. In our example, we'll simply concatenate the certificate and key files together (in that order) to create a xip.io.pem file. This is HAProxy's preferred way to read an SSL certificate.
When purchasing a real certificate, you won't necessarily get a concatenated 'bundle' file. You may have to concatenate them yourself. However, many do provide a bundle file. If you do, it might not be a pem file, but instead be a bundle, cert, cert, key file or some similar name for the same concept. This Stack Overflow answer explains that nicely.
In any case, once we have a pem file for HAproxy to use, we can adjust our configuration just a bit to handle SSL connections.
We'll setup our application to accept both http and https connections. In the last edition on HAProxy, we had this frontend:
To terminate an SSL connection in HAProxy, we can now add a binding to the standard SSL port 443, and let HAProxy know where the SSL certificates are:
In the above example, we're using the backend 'nodes'. The backend, luckily, doesn't really need to be configured in any particular way. In the previous edition on HAProxy, we had the backend like so:
Because the SSL connection is terminated at the Load Balancer, we're still sending regular HTTP requests to the backend servers. We don't need to change this configuration, as it works the same!
SSL Only
If you'd like the site to be SSL-only, you can add a redirect directive to the frontend configuration:
Above, we added the redirect directive, which will redirect from 'http' to 'https' if the connection was not made with an SSL connection. More information on ssl_fc is available here.
HAProxy with SSL Pass-Through
With SSL Pass-Through, we'll have our backend servers handle the SSL connection, rather than the load balancer.
The job of the load balancer then is simply to proxy a request off to its configured backend servers. Because the connection remains encrypted, HAProxy can't do anything with it other than redirect a request to another server.
In this setup, we need to use TCP mode over HTTP mode in both the frontend and backend configurations. HAProxy will treat the connection as just a stream of information to proxy to a server, rather than use its functions available for HTTP requests.
First, we'll tweak the frontend configuration:
This still binds to both port 80 and port 443, giving the opportunity to use both regular and SSL connections.
As mentioned, to pass a secure connection off to a backend server without encrypting it, we need to use TCP mode (mode tcp) instead. This also means we need to set the logging to tcp instead of the default http (option tcplog). Read more on log formats here to see the difference between tcplog and httplog.
Next, we need to tweak our backend configuration. Notably, we once again need to change this to TCP mode, and we remove some directives to reflect the loss of ability to edit/add HTTP headers:
As you can see, this is set to mode tcp - Both frontend and backend configurations need to be set to this mode.
We also remove option forwardfor and the http-request options - these can't be used in TCP mode, and we couldn't inject headers into a request that's encrypted anyway.
For health checks, we can use ssl-hello-chk which checks the connection as well as its ability to handle SSL (SSLv3 specifically) connections.
In this example, I have two fictitious server backend that accept SSL certificates. If you've read the edition SSL certificates, you can see how to integrate them with Apache or Nginx in order to create a web server backend, which handles SSL traffic. With SSL Pass-Through, no SSL certificates need to be created or used within HAproxy. The backend servers can handle SSL connections just as they would if there was only one server used in the stack without a load balancer.
Resources
Haproxy For Windows Download

- HAProxy Official blog post on SSL Termination
- SO Question: 'What is a PEM file?'
- Reading custom headers in Nginx - Not mentioned in this edition specifically, but useful in context of reading
X-Forwarded-*headers sent to Nginx - So You Got Yourself a Load Balancer, an article about considerations to make in your applications when using a load balancer.
Ready to get going? Start your 14 days free trial today
Start free trialHave an account?Sign in

Haproxy Rpm
Metricbeat is a lightweight shipper that helps you monitor your HAProxy servers by collecting metrics from the HAProxy server. Configure Metricbeat using the pre-defined examples below to collect and ship HAProxy service metrics and statistics to Logstash or Elasticsearch.
Step 1 - Install Metricbeat
First we need to install Metricbeat.
deb (Debian/Ubuntu)
rpm (Redhat/Centos)
macOS
Windows
Download the Metricbeat Windows zip file from the official downloads page.
Extract the contents of the zip file into C:Program Files.
Rename the
metricbeat-<version>-windowsdirectory toMetricbeat.Open a PowerShell prompt as an Administrator (right-click the PowerShell icon and select Run As Administrator). If you are running Windows XP, you may need to download and install PowerShell.
Microsoft office document imaging download xp. Run the following commands to install Metricbeat as a Windows service:
PowerShell.exe -ExecutionPolicy UnRestricted -File .install-service-metricbeat.ps1.deb/rpm/etc/metricbeat/metricbeat.yml
mac/win<EXTRACTED_ARCHIVE>/metricbeat.yml
Step 3 - Configure output
Haproxy For Windows
We'll be shipping to Logstash so that we have the option to run filters before the data is indexed.
Comment out the elasticsearch output block.
Uncomment and change the logstash output to match below.
There are several built in metricbeat modules you can use. To enable the HAProxy module, run the following:
deb/rpm
macOS
Windows
Step 5 - Configure module
Each module has its own configuration file where different metricsets can be enabled / disabled. Locate the configuration file for the HAProxy module.
deb/rpm/etc/metricbeat/modules.d/haproxy.yml

mac/win~/<EXTRACTED_ARCHIVE>/modules.d/haproxy.yml
By default the info and stat metricsets are disabled. To enable or disable a metric simply comment or uncomment the line out.
Haproxy Load Balancer
Ok, time to start gathering metrics!
deb/rpm
macOS
Haproxy Example Config
Windows
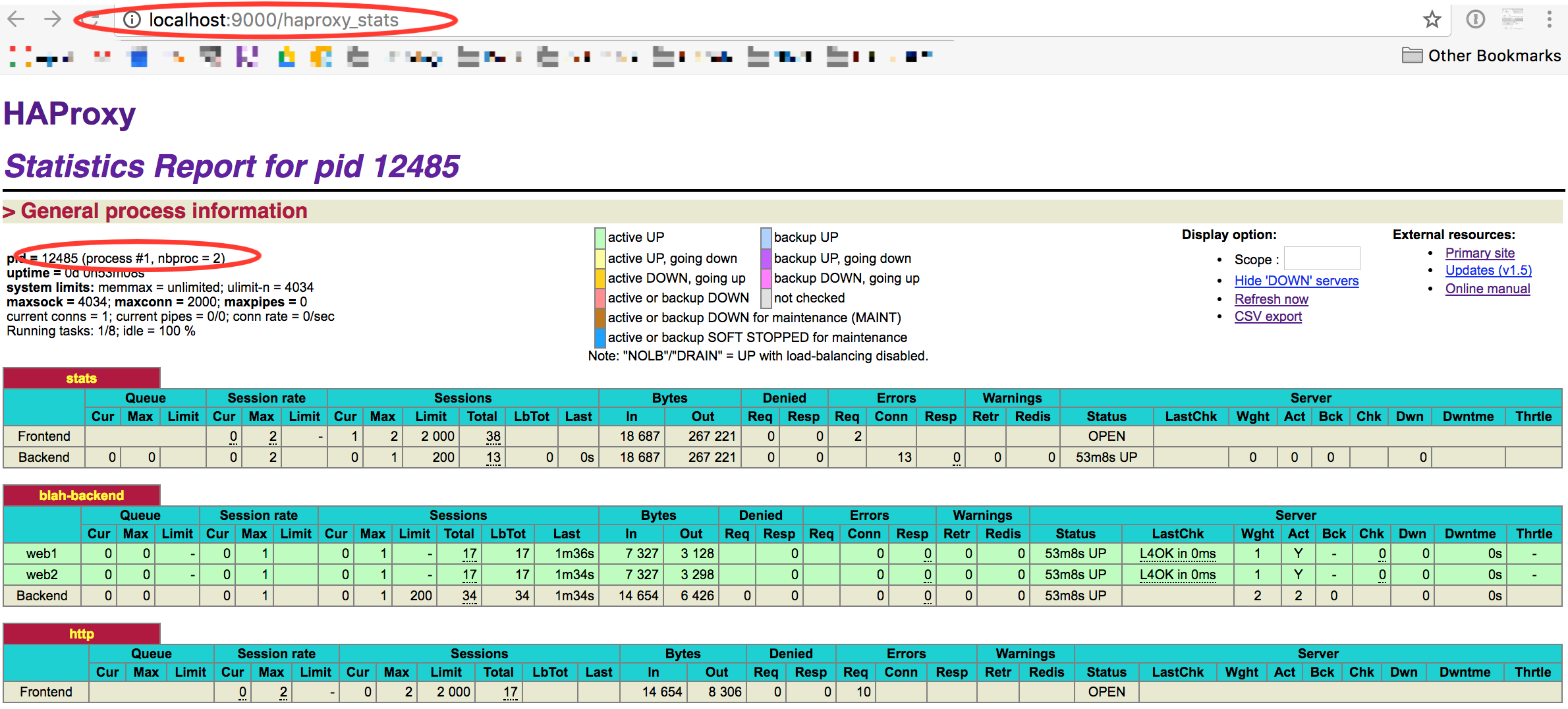
Step 7 - Compatibility
The HAProxy metricsets are tested with HAProxy versions 1.6, 1.7 and 1.8.